Next named exclusive Trail Blazer in NEW 2024 Radicati DLP Market Quadrant Report
Read the Report


As businesses send their employees to work from home, it's imperative for security professionals to provide guidance so remote workers can do their part to help you keep your organization secure and protected from breaches. With Reveal, organizations get visibility of their data and endpoints outside of the office.

Get full visibility of your data and endpoints outside of the office. Reveal notifies organizations of unencrypted or unapproved Wi-Fi networks, suspicious login activity, or printing outside office hours, geolocation, and more.
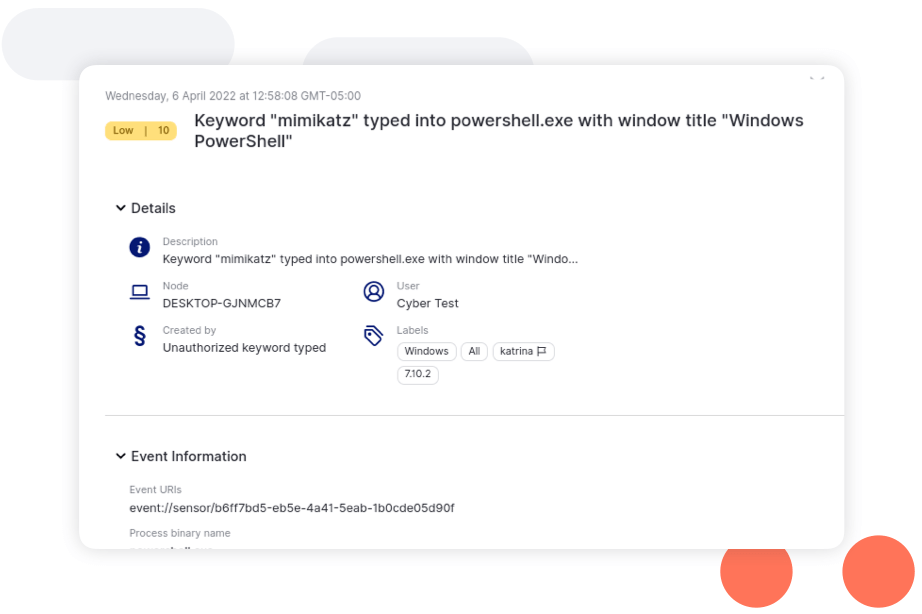
Organization-owned computers are increasingly used for both work and personal use. Using advanced mechanisms such as keystroke analytics, Reveal can detect when computers are shared with others, and even spot credential sharing.
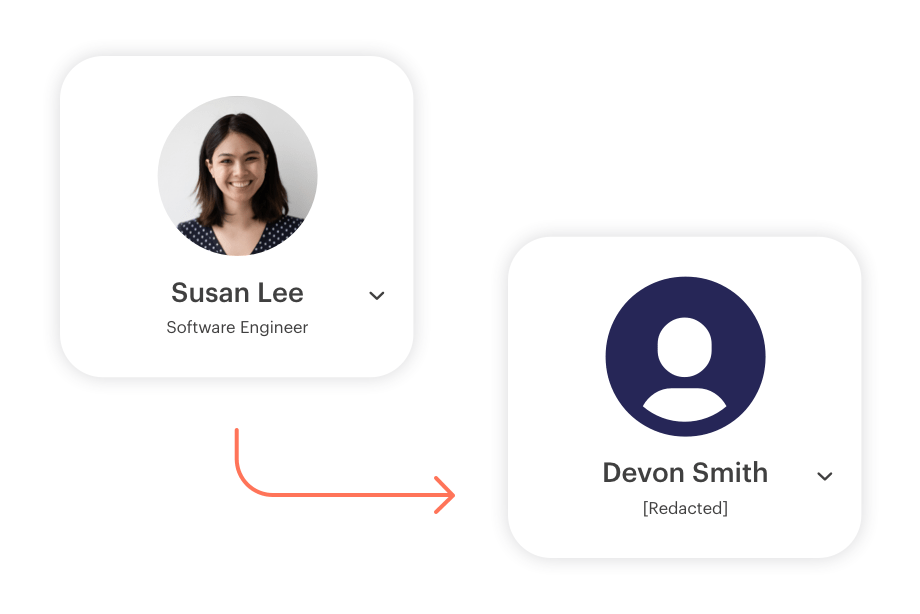
With Next DLP’s industry-leading solution of pre-built data minimization techniques, such as pseudonymization and anonymization (partial and full redaction), you can now detect and mitigate threats while maintaining the confidentiality of users.
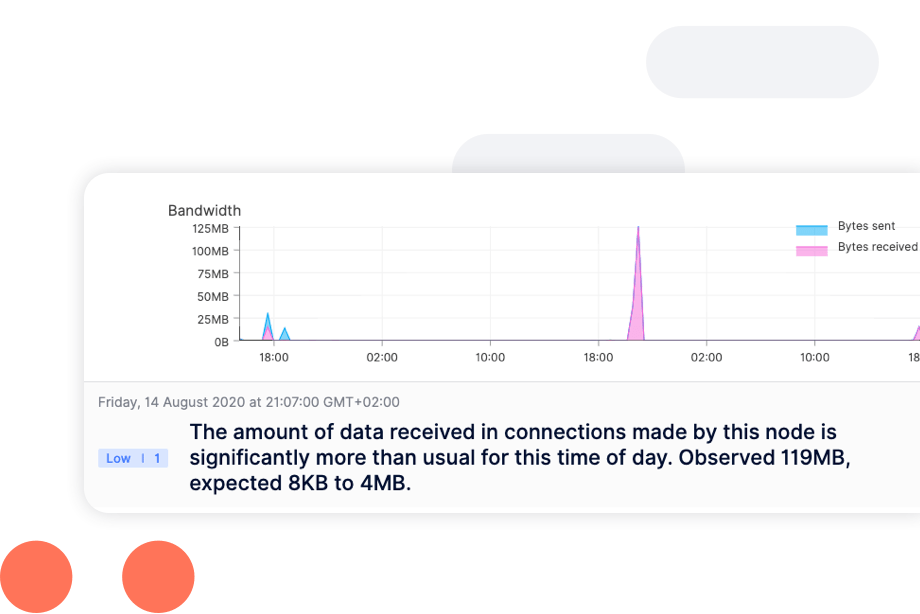
Combining these two powerful methods of detection, regardless of an employee being offline or remote. This combination analyzes more user scenarios and detects more incidents–resulting in faster threat remediation.
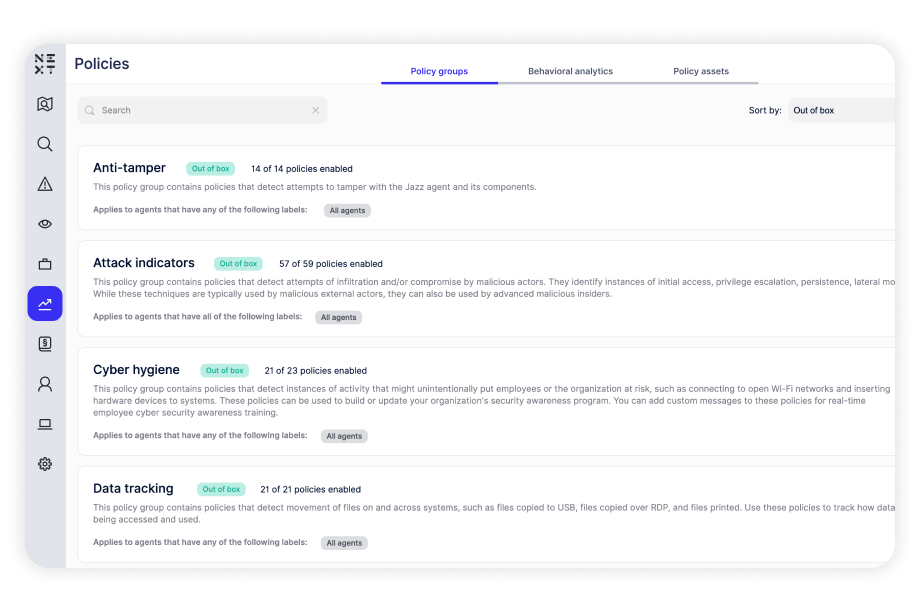
Built-in policies for data tracking, cyber hygiene, and malicious activity that can detect and defend against various risks. Policies run against computers and users, providing insight into how users access files, applications, and systems, which determine specific areas of risk.

The Reveal agent is deployed to Windows, macOS, and Linux computers and servers, where it collects granular behavioral information for security threat analysis.
