Next named exclusive Trail Blazer in NEW 2024 Radicati DLP Market Quadrant Report
Read the Report


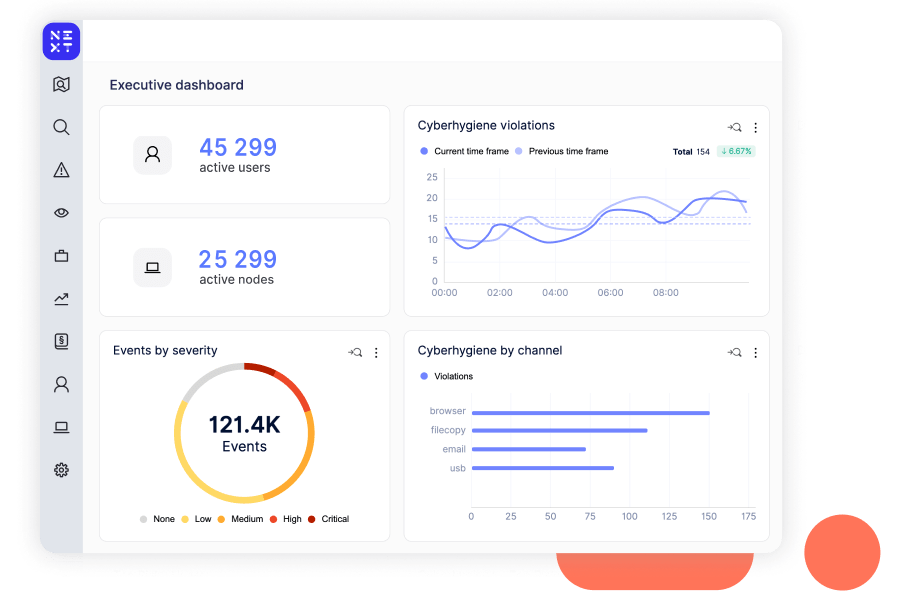
Most CISOs utilize multiple security technologies within their organizations to survive. As a result, under-resourced IT teams are often stretched too thin trying to manage and optimize these investments. Reveal is a security multiplier, enhancing threat detection and response across your ecosystem with unprecedented visibility, behavioral analytics and adaptive control. It delivers the situational awareness and integrations to improve enterprise-wide security ROI.
Individual user profiles shed light on how data is accessed and used, with optional anonymization for privacy. With user activity monitoring, you can protect your systems and data from those who already have privileged access and knowledge of sensitive data and systems.
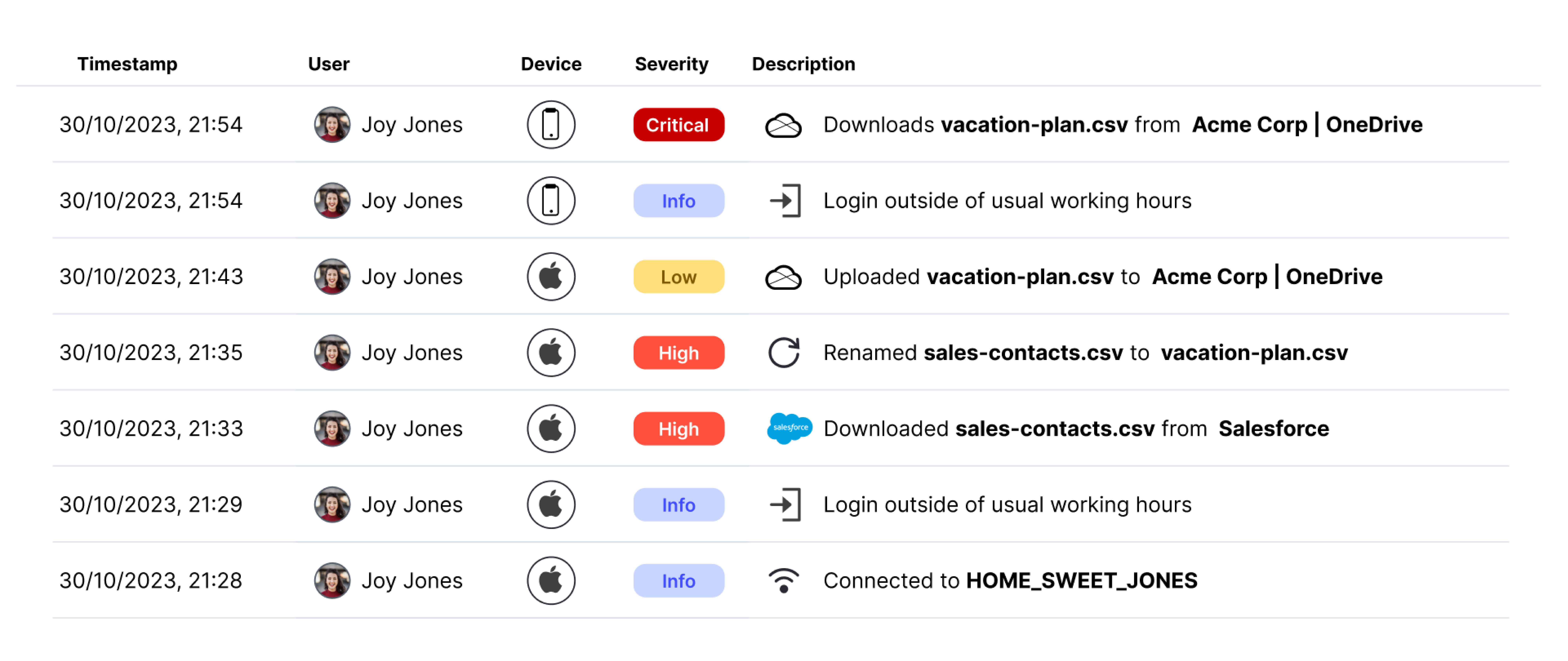
Reveal Beyond overcomes legacy DLP challenges by providing a unified platform for managing data security and extending insider threat visibility and data protection to Microsoft O365, Google Workspace and personal devices.
Reveal Beyond doesn’t require endpoint agents or on-prem technology and effectively addresses DLP and insider risk use cases commonly seen with the use of cloud drives and unmanaged personal devices. Investigation and remediation processes are streamlined to reduce exposure to security risks and compliance challenges.
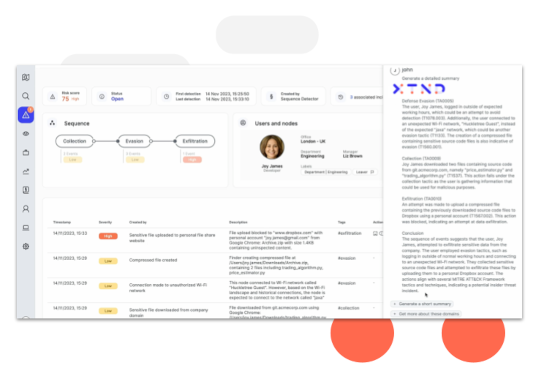
Reveal's AI powered assistant, XTND, extends insider risk and data security analysts’ expertise, enabling every member of the security team to contribute to the business at a higher level.
High risk insider activity is contextualized, summarized and presented to the analyst in an easy-to-consume way.
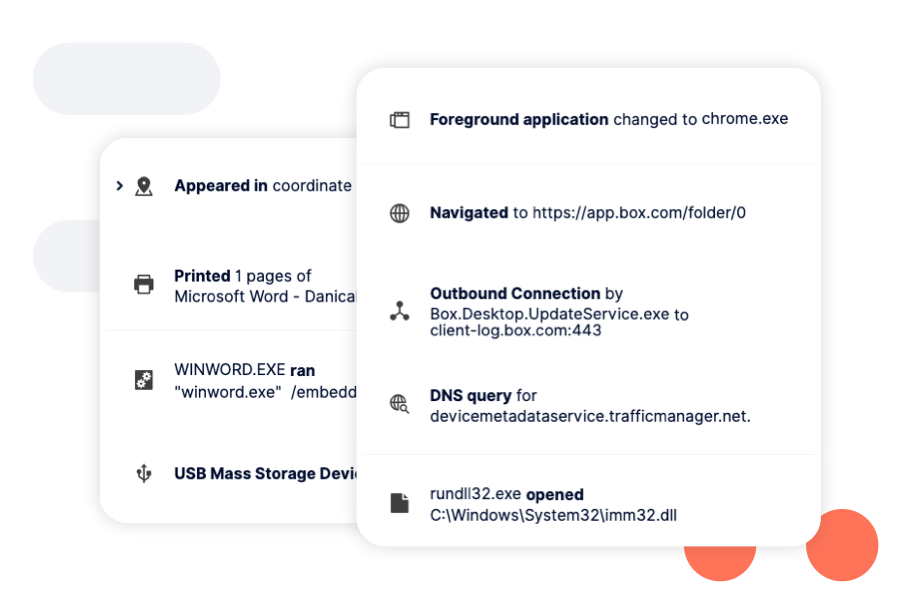
Built-in rules immediately alert the operator of real-world insider risk scenarios. For example, detect employees using restricted administrative tools, sending sensitive information outside of the organization, circumventing security, and printing documents during irregular hours.
Reveal SaaS Access Security provides comprehensive insights into the use of SaaS applications throughout an organization, enhancing security measures to protect against data breaches caused by unauthorized application usage and potential exposure of business data.
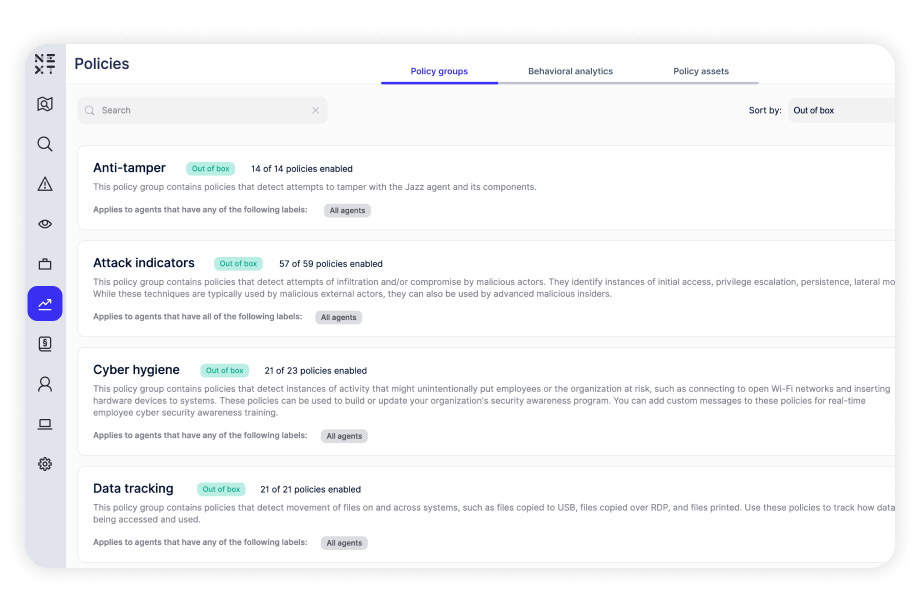
Built-in policies for data tracking, cyber hygiene, and malicious activity that can detect and defend against various risks. Policies run against computers and users, providing insight into how users access files, applications, and systems, which determine specific areas of risk.
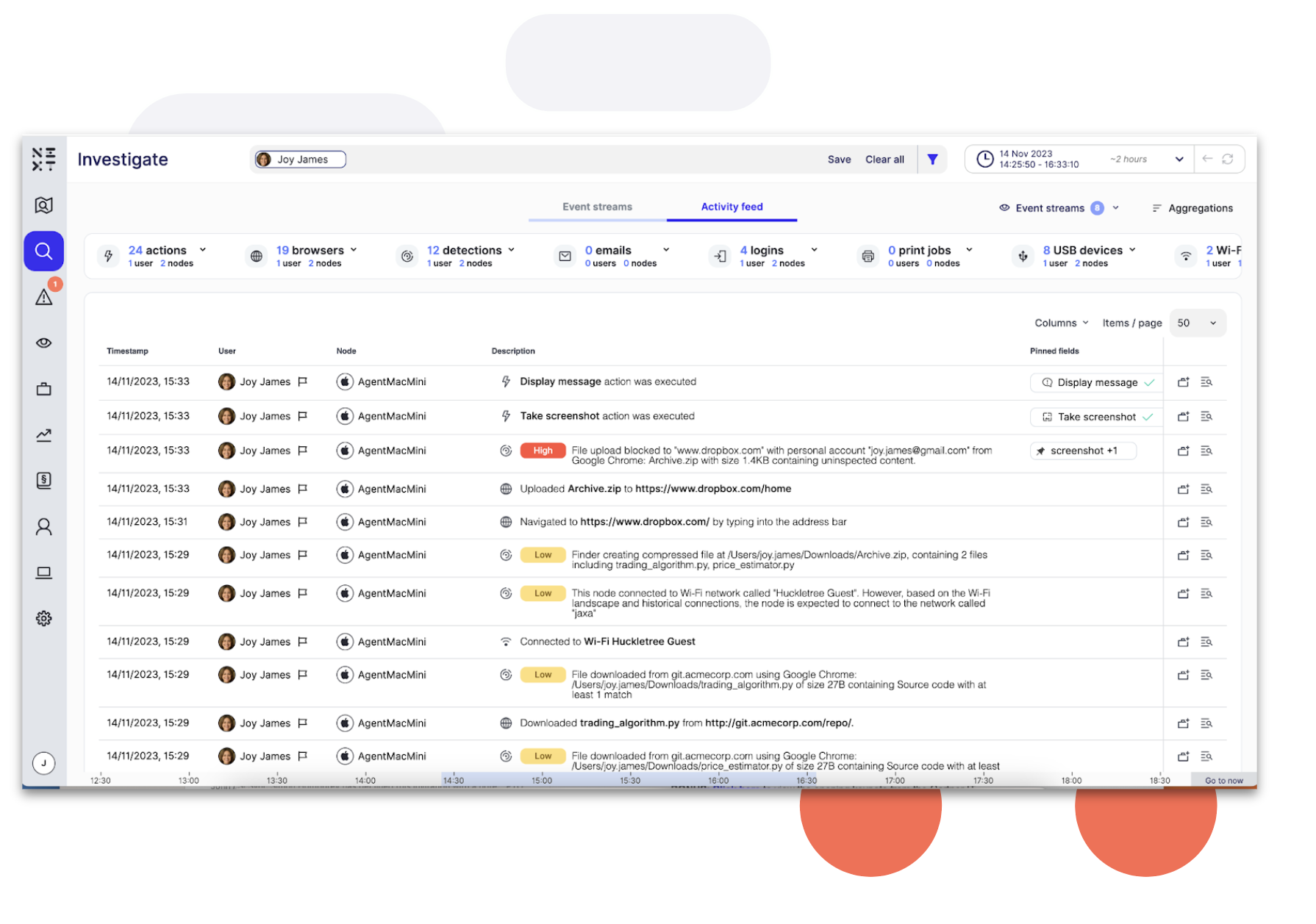
Continuous monitoring provides visibility into user behaviour, data access, and system use. Security operators can search on file, USB device, connection, browser, application events, and more.
Content and context based reporting across all touchpoints.
Activity Feed provides analysts with a comprehensive, streamlined and time sequenced view of user, data and device activity before, after and during an incident.
With Next DLP’s industry-leading solution of pre-built data minimization techniques, such as pseudonymization and anonymization (partial and full redaction), you can now detect and mitigate threats while maintaining the confidentiality of users.

Reveal is UAM certified by National Insider Threat Task Force (NITTF), providing individual user profiles, keystroke visibility, full application content, and screen capture. All data is attributed to a specific user, even on shared machines.
