Next named exclusive Trail Blazer in NEW 2024 Radicati DLP Market Quadrant Report
Read the Report


Executives hate surprises, particularly unforeseen data events. The Reveal Platform from Next DLP learns what normal data movement and use look like in your environment, distinguishing between a user mistake and malicious intent. It protects critical assets on and off the network, providing the visibility and control to prevent data loss in business-critical applications. Where before you lacked true insight into the risks posed by users and their devices, now you know.
Data protection with dynamic responses, from ingress to egress, on managed and unmanaged devices.
Instant-on endpoint and cloud sensors provide visibility without policy.
The lightweight Reveal agent has minimal impact on employees’ productivity, performing incident-based training, advanced content inspection, policies, machine learning, and automated enforcement.
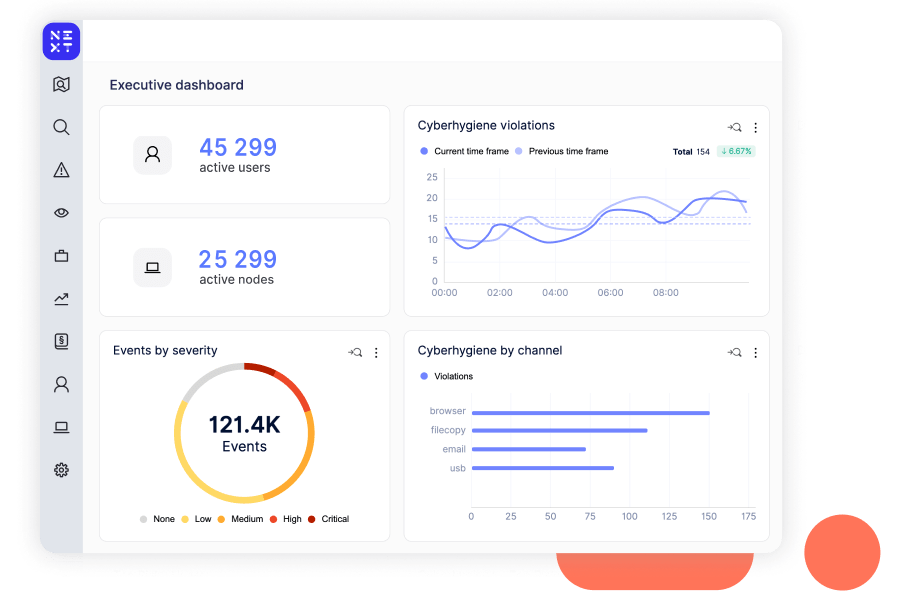
Reveal's AI-powered assistant, XTND, takes security analysts to the next level with streamlined data loss and insider threat analysis.
XTND enhances incident analysis by using GenAI to summarize and contextualize data associated with observed high risk activity, mapped to MITRE IT TTP, for easy consumption by analysts.
Analysts benefit from optimized workflows, a reduction in time to contain and resolve threats, and the empowerment to contribute to the business at a higher level.
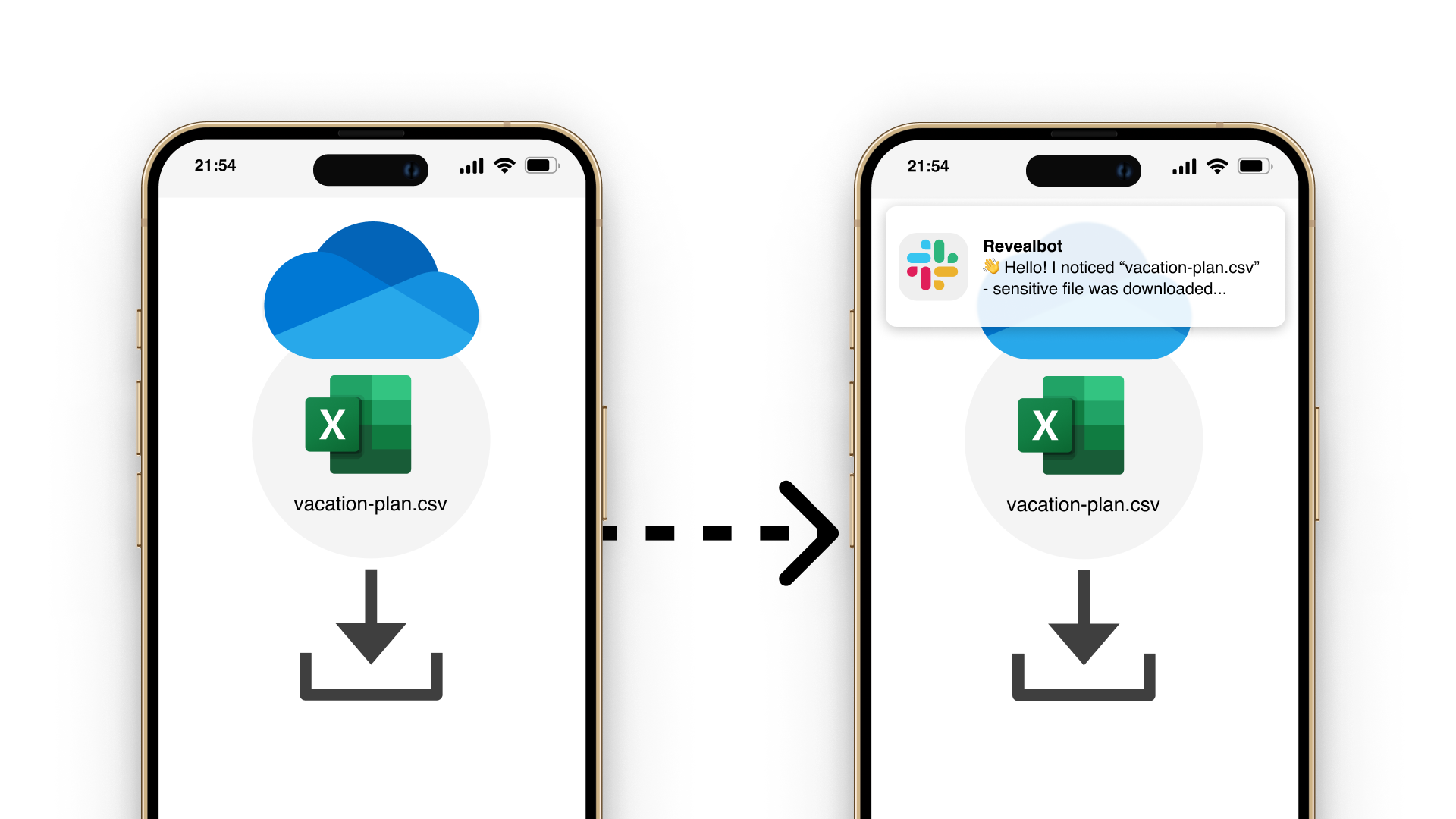
Reveal Beyond overcomes legacy DLP challenges by providing a unified platform for managing data security and extending insider threat visibility and data protection to Microsoft O365, Google Workspace and personal devices.
Reveal Beyond doesn’t require endpoint agents or on-prem technology and effectively addresses DLP and insider risk use cases commonly seen with the use of cloud drives and unmanaged personal devices. Investigation and remediation processes are streamlined to reduce exposure to security risks and compliance challenges.
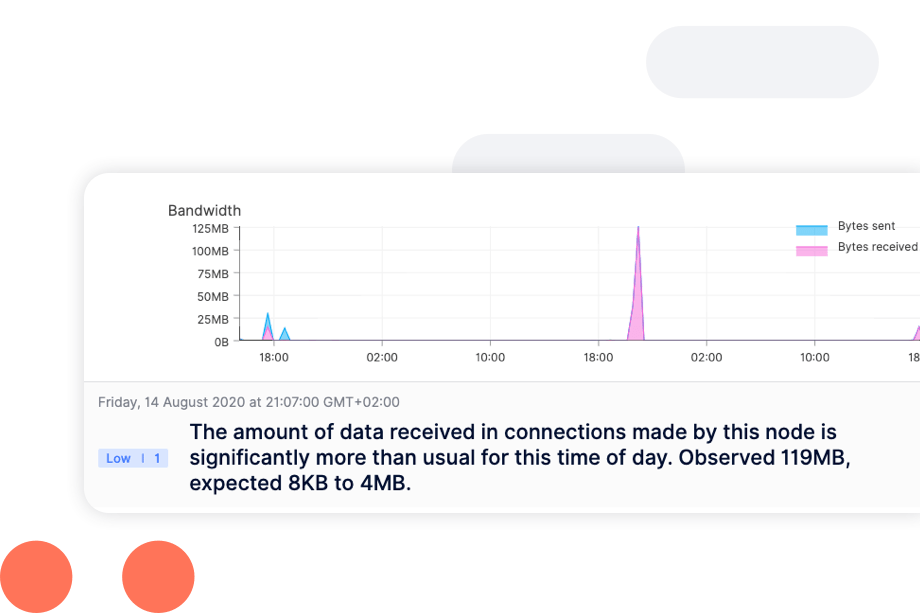
Constant enforcement without exception–whether they are remote or working offline. Enforcing employee adherence to corporate policies such as Acceptable Use Policy (AUP), Information Security Policy (ISP) and more.
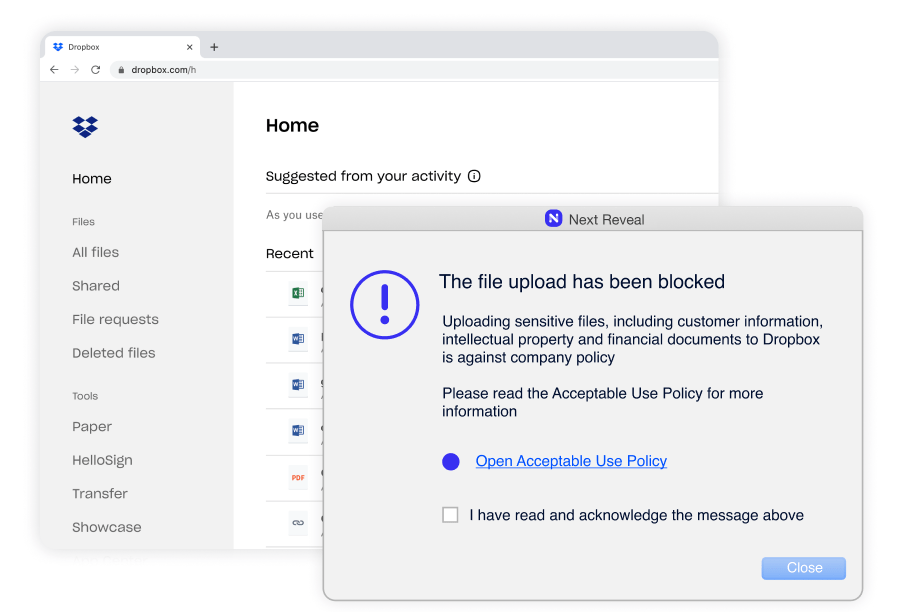
Machine learning and smart sensors detect risks before they become incidents, even when employees are offline or remote. This combination analyzes more user scenarios and detects more incidents–resulting in faster threat remediation.
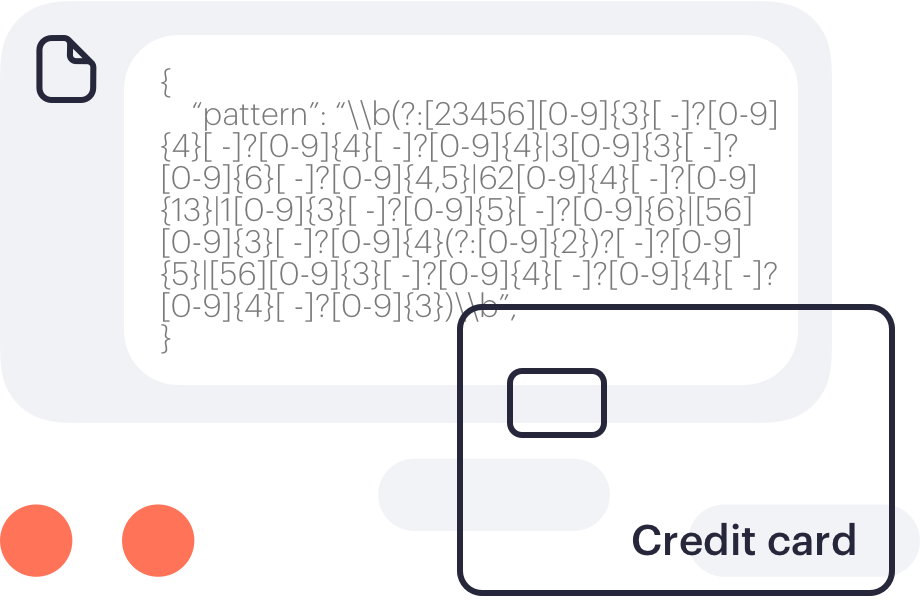
Track file movement on and across systems and browsers with advanced content inspection to protect against data loss. Patterns include credit or debit card numbers, identity card numbers, insurance numbers, social security numbers, and national health service numbers.
