Next named exclusive Trail Blazer in NEW 2024 Radicati DLP Market Quadrant Report
Read the Report

Compliance is becoming more complex every year with new and updated laws, regulations, and security standards such as GDPR, HIPAA, PCI DSS, ISO 27001, NIST, and more.
Managing the risk factors of compliance is a challenge, especially making sure employees adhere to the required standards. Organizations have laws determined by geographical area as well as regulations set by the industry. For example medical services need to protect personally identifiable information (PII) and protected health information (PHI) and comply with HIPAA and GDPR depending on the location. Companies which must be PCI compliant to access credit card information need visibility of who accesses credit card data. Failing to comply with these regulation carries both financial and reputational risk.
In addition, as compliance audits have a retrospective approach looking at previous incidents, many organizations want to shift to a proactive approach to ensure compliance ahead of the audit.
GDPR also includes a right to privacy for the employees, making it challenging for some security solutions to properly detect and mitigate threats as they only see part of the bigger picture.
With Reveal you can take a proactive approach to your compliance audits, enforcing compliance laws and regulations to change employee behavior with visibility to users, data access and systems–with the option of anonymizing the data.

Individual user profiles shed light on how data is accessed and used, with optional anonymization for privacy. With user activity monitoring, you can protect your systems and data from those who already have privileged access and knowledge of sensitive data and systems.
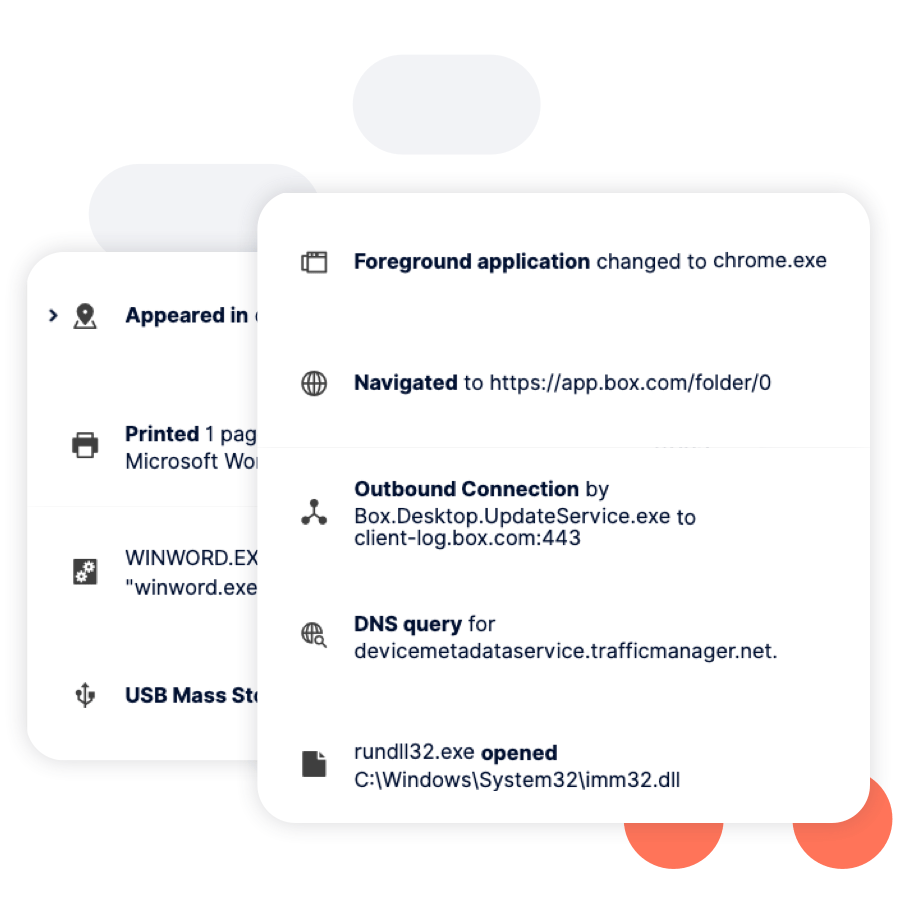
Continuous monitoring provides visibility into user behaviour, data access, and system use. Security operators can search on file, USB device, connection, browser, application events, and more.
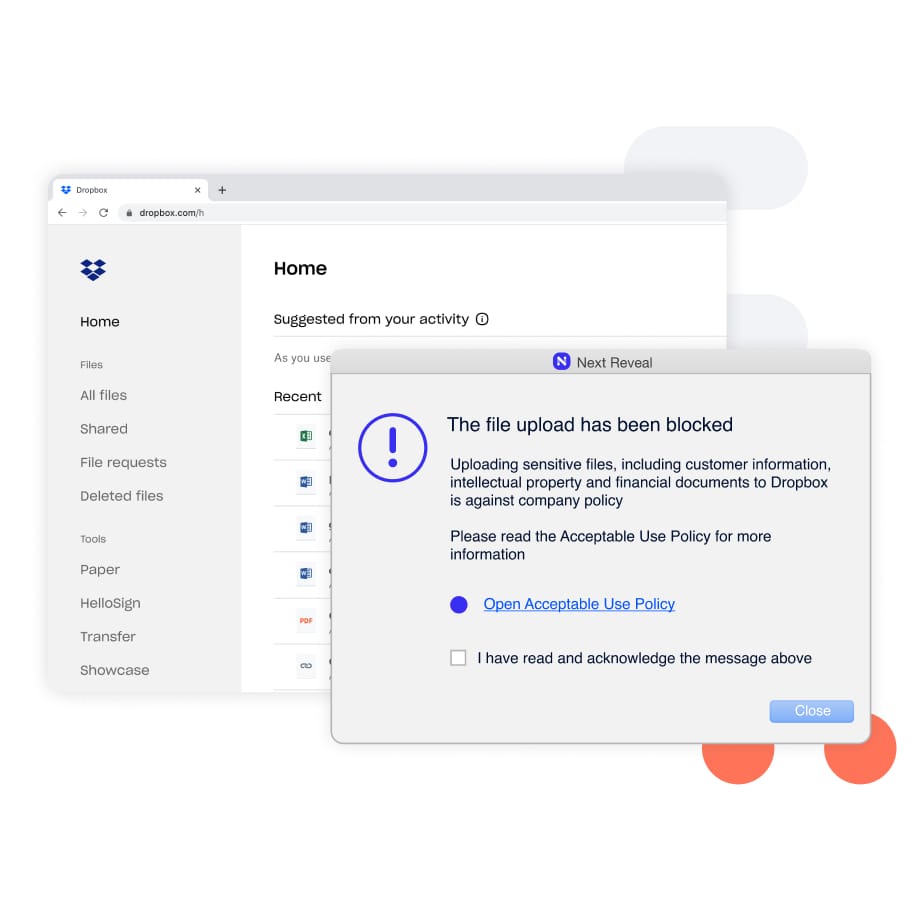
Constant enforcement without exception–whether they are remote or working offline. Enforcing employee adherence to corporate policies such as Acceptable Use Policy (AUP), Information Security Policy (ISP) and more.
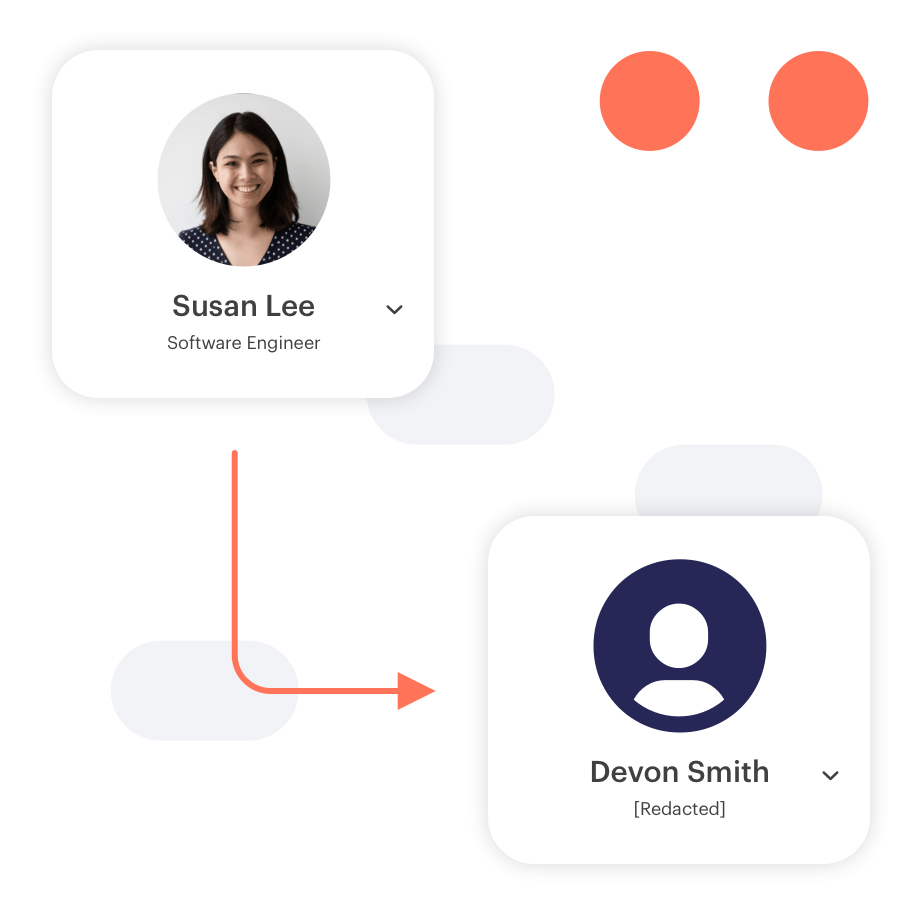
With Reveal's industry-leading solution of pre-built data minimization techniques, such as pseudonymization and anonymization (partial and full redaction), you can now detect and mitigate threats while maintaining the confidentiality of users.
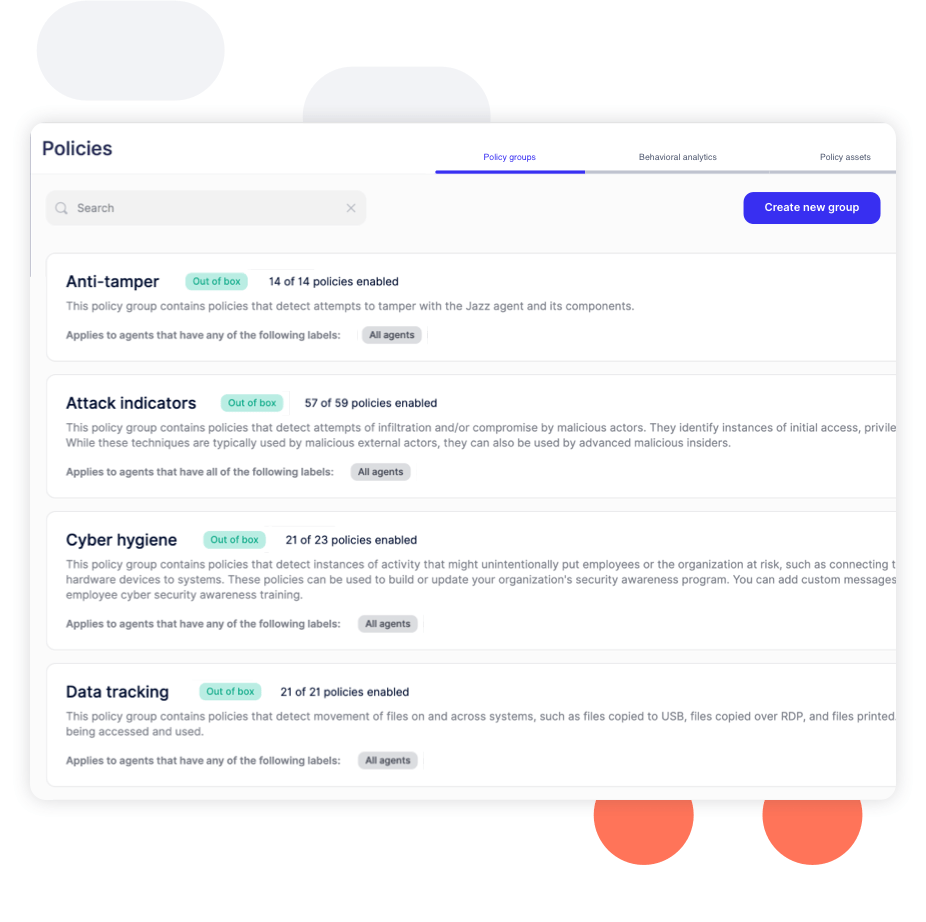
Built-in policies for data tracking, cyber hygiene, and malicious activity that can detect and defend against various risks. Policies run against computers and users, providing insight into how users access files, applications, and systems, which determine specific areas of risk.
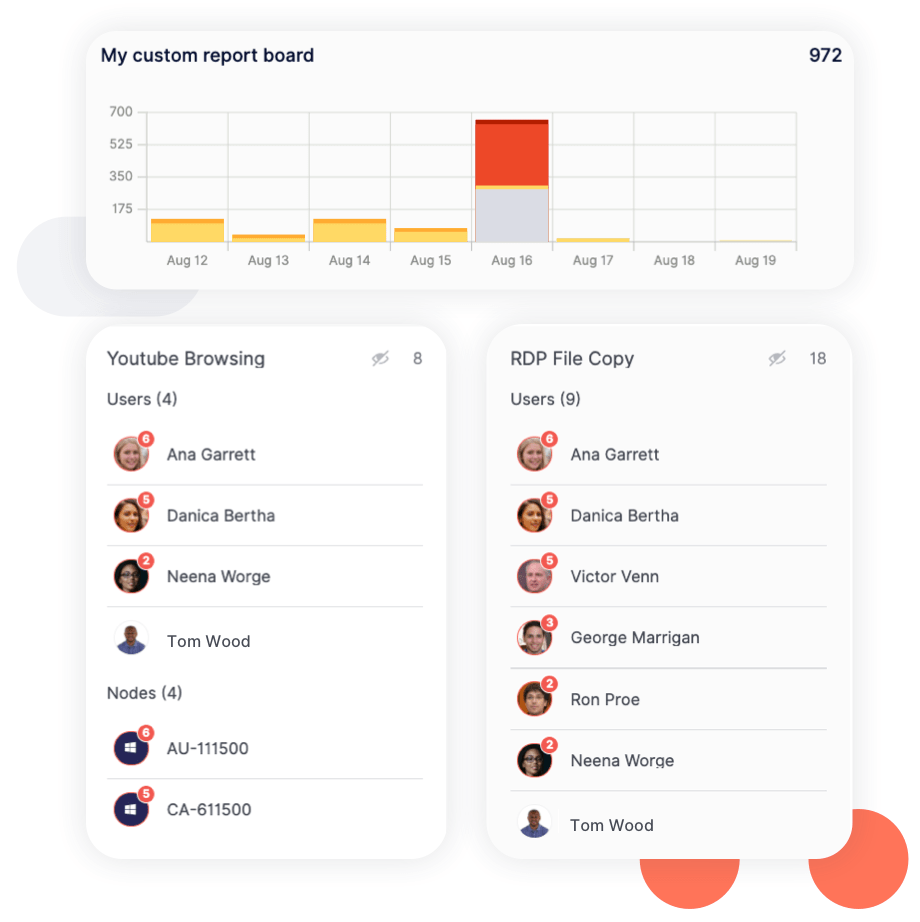
Reports highlight instances of careless, malicious, and accidental behavior over time, allowing you to assess the effectiveness of your security controls and identify areas for improvement. Reports can also be easily exported to share with leadership.

Blog

Blog

Blog

Blog

Resources

Resources

Resources

Resources
